Presentation
Attack Prevention
Anti-spoofing Technology Light Years Ahead of its Time

Presentation Attack Detection (PAD)
Everybody wants to beat the system. That’s especially true for criminals faced with biometric fingerprint scanners. Methods commonly used to counter biometric fingerprint security include the production of counterfeit fingerprints and fingers, or the presentation of severed digits.
Presentation attack detection, or PAD, is the comprehensive approach to spoof-detection which includes both anti-spoofing and liveness detection technologies. Both are discrete methods to combating biometric fraud, and each is optimized to resolve a distinct issue. Anti-spoofing refers to the detection of an artificial copy of a real or synthetic fingerprint. Liveness detection refers to the validation of human tissue as belonging to that of a living human being.

Conductive Spoofs vs. Non-Conductive Spoofs
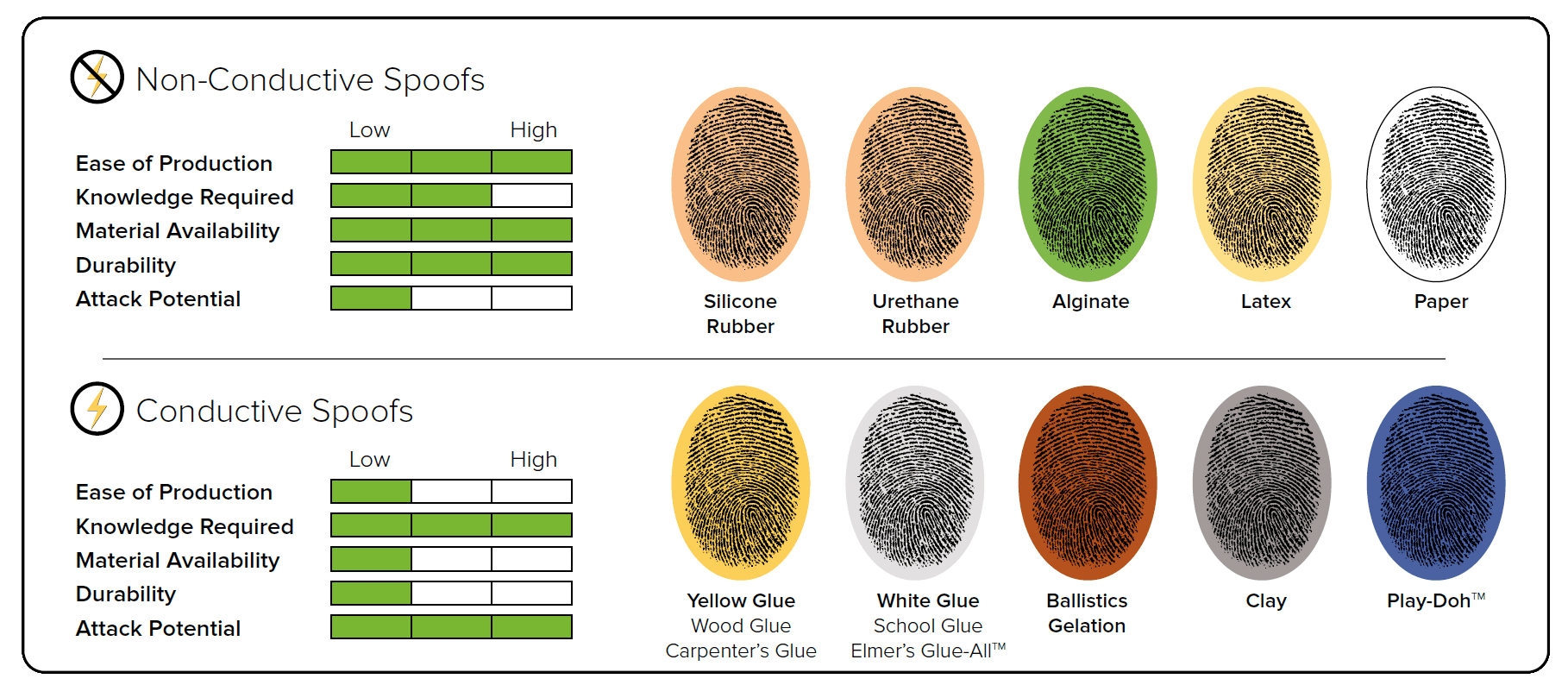
10 common spoof types we believe customers with biometric fingerprint systems may encounter in their environments.
In general, spoofs can be divided into 2 categories: non-conductive and conductive.
Non-conductive spoofs possess electrical characteristics that better simulate genuine human fingerprints. These advanced spoofs are less common due to the additional knowledge and tools needed to produce them.
These materials regularly retain artifacts from their manufacture which makes them more susceptible to detection by PAD techniques.
Conductive spoofs possess electrical characteristics that better simulate genuine human fingerprints. These advanced spoofs are less common due to the additional knowledge and tools needed to produce them.
These spoofs often retain the most tissue-realistic characteristics and present the highest degree of attack potential.
The IB Approach
Integrated Biometrics’ LES film technology already provided automatic spoof rejection, but the value of the information and systems protected were causing threat actors to step up their game, requiring us to raise the stakes in our Presentation Attack Detection.
Integrated Biometrics’ approach to presentation attack detection is tiered verification. The first tier is hardware: LES film in IB scanners instantly rejects any non-conductive presentation attack, which nullifies the threat of the most common spoof constructions.
The second tier is software: a unique deep-learning AI algorithm trained to detect anomalies in fingerprints typical of spoof attacks discerns a liveness score with a high degree of accuracy. This PAD technique is completed in milliseconds with a latency that is imperceptible to the end user.
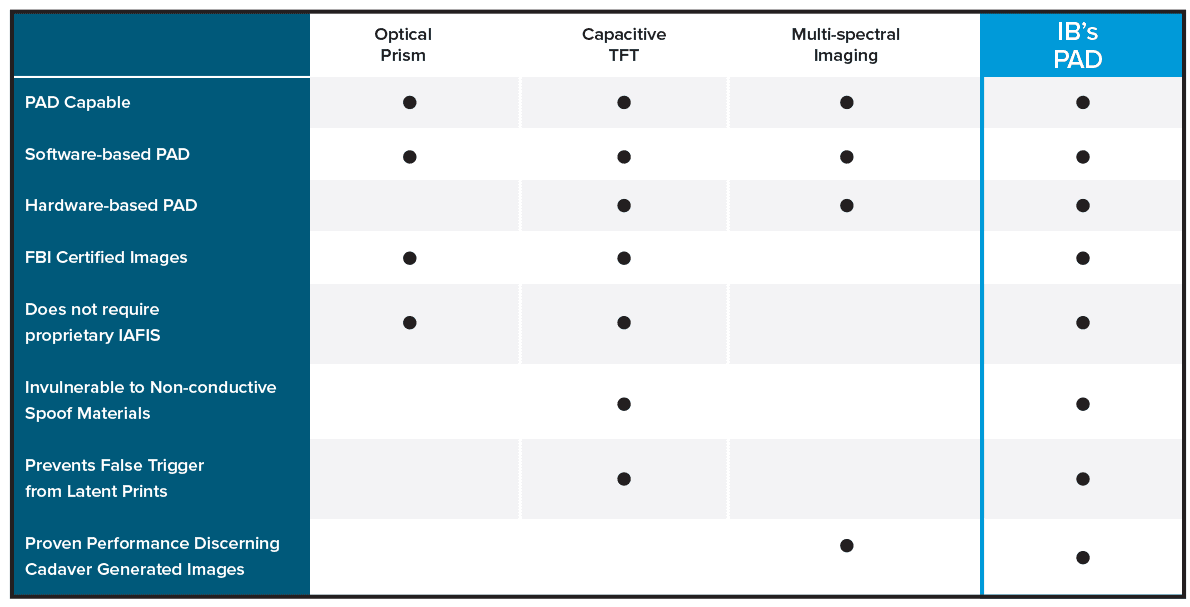
What’s In Your Scanner?
Expected Performance
Here is the overall EER of an IB scanner equipped with PAD, which we believe is representative of expected performance in the real world.
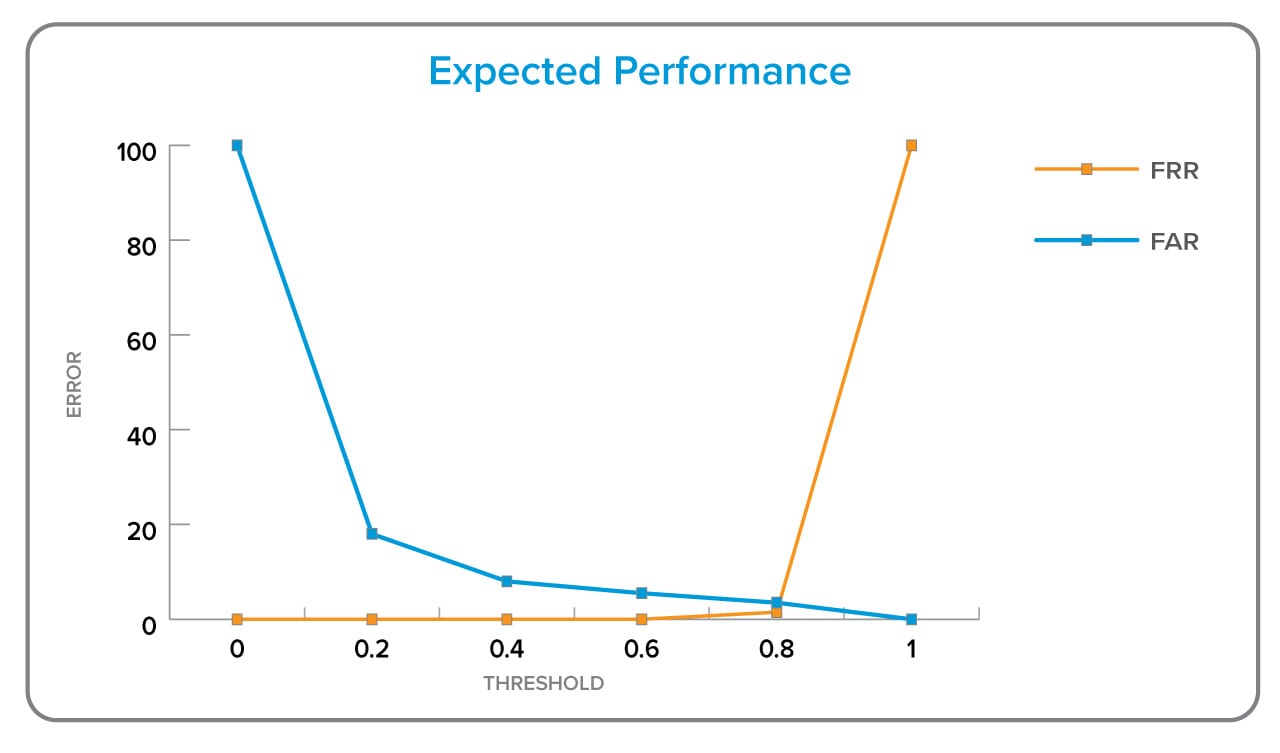
In the example above, the aggregate EER was an unmatched 1.58% at a threshold of 0.907. Based on our earlier metric for judging percent error, out of 100 different spoofs presented, a user might see 1 or 2 make it through successfully. Out of 100 presentations of genuine fingerprints, a user could expect to be asked to re-enter their fingerprint 1 or 2 times.
Contact Us
"*" indicates required fields
